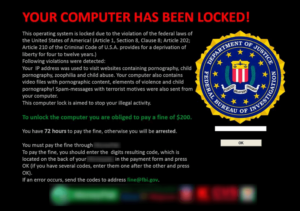
There is a major RANSOMWARE attack on-going in more than 70 countries
This was first reported May 13th 2017 and over 100 countries have been affected.
The attack favors Microsoft Window machines. According to Microsoft if you use their auto-updating feature then you recieved the security update that protects you against this particular attack. If you don’t, UPDATE IMMEDIATELY!!
Ransomware
An article appeared with this very title about Ransomware on the Financial Executives International website by Dave Pelland on April 25th, 2017. I then brought up the subject (again) about cyber security, ransomware, data backups on the CFO website Proformative.com. And yet, the response from the CFO community has been tepid.
There are so many scams. The fake IT department calling and requesting your IP address. Why? To malware embedded in websites and email. The unwary, non-proficient or the just a disgruntled person can fall victim to many different scams. Once you fall victim, the consequences can become devastating.
What can go wrong?
Where do we begin. Files that become encrypted. Stolen data. Using your system as a springboard for spreading the criminal act. Not only will they be using your equipment, but your database of email addresses and possibly your brand as well.
Hours, days, weeks can be spent sanitizing your systems and data (if you are lucky enough to recover your data). The cost of repair. The ransom should the criminals encrypt your files can be hefty. These days they ask for bitcoin, because it is nearly impossible to trace. But what about lost business and as mentioned, the damage to your brand.
Who’s been hacked?
Here’s a list from Fortune Magazine based on 2013-2015:
Premera Blue Cross, Anthem, CareFirst BlueCross BlueShield, Ashley Madison, US Dept of Personnel, Home Depot, JP Morgan, EBay, Target and the list goes on. As a customer of several of those entities wasn’t pleased. I am sure you share that feeling. If you were thinking of using them, they had at least a momentary second thought.
It’s now 2017 and how many on this list do you still remember hearing about? I can say six off the top of my head. Let’s not forget Yahoo.
According to the Heritage Foundation in 2015/2016 these entities were victims of cyber attacks: Bowman Dam, Hyatt Hotels, MacKeeper, A Whole Lot of Nothing LLC, Alliance Health, The Wendy’s Company, U.S. Department of Homeland Security, Federal Bureau of Investigation,Verizon Enterprise Solutions, LinkedIn, Democratic National Committee, Citibank, Dropbox, US Voter information, Oracle MICROS and the list goes on…
Why does one not believe it can happen to your company or your household?
What can you do?
There are several simple steps. This is not all inclusive, but it will go a long way to shielding most.
- Strong Passwords
- Some type of Anti-Virus/Malware software
- Backups of your files (and segregation by day, week and month)
- Don’t open attachments and unless you know the person.
- Double check the “from” address and make sure it is accurate (not a clever spoof).
- Think before you click a link.
- Think before you give a person who calls out of the blue information.
- Be cynical!
As an example: Forrester Research1 has this to say about backups:
› Focus on frequent and clean backups.
To defeat ransomware with backups, focus on two significant areas: frequency and cleanliness. Ransomware is effective if companies don’t have backups that are recent enough to restore data and keep the business running. Additionally, it should be noted that the backup must be clean. This means that the malware has not already infected the device, which will transfer the malware to the backup, and restoration will lead to new ransomware infections.
› Schedule frequent backups.
Out of the hospitals that have been hit with ransomware attacks, those that avoided paying ransom were the ones with solid data backups.29 It’s true! Cybercriminals can’t hold your data hostage and extort you for ransom if you have another copy of it. Work with your infrastructure and operations counterparts to build and implement a backup and disaster recovery plan.30 Just make sure that once you’ve implemented it, you’re testing it frequently and using a variety of test types.31
› Watch backups for malware.
Make sure that you know that a machine or device is not currently infected with malware before backing it up. For example, automated file sync solutions may not be an effective backup method because the malware will be immediately synced and the whole backup will be infected. File synchronization solutions are powerful and important, but they should not be used as a replacement for more traditional backup solutions.
If you are a business, start having the discussion yesterday, not tomorrow about your disaster recovery plans. By the way, SBA * Consulting can help! Our Cybersecurity and Incident and Crisis Management Teams can assist!